tl;dr - avast’s web shield functionality appears to insert itself into SSL connections using a self signed trusted root certificate and a simple kind of man-in-the middle “attack” on SSL. I would recommend you turn off web shield’s https scanning or choose another virus scanner.
I read about this on a blog post that was linked from Hacker News where someone claimed that Avast’s virus scanner for Mac OS inserts itself into SSL-encrypted connections using a self-signed certificate. A quick check on a Windows machine in my household confirmed that this was also true for Windows:
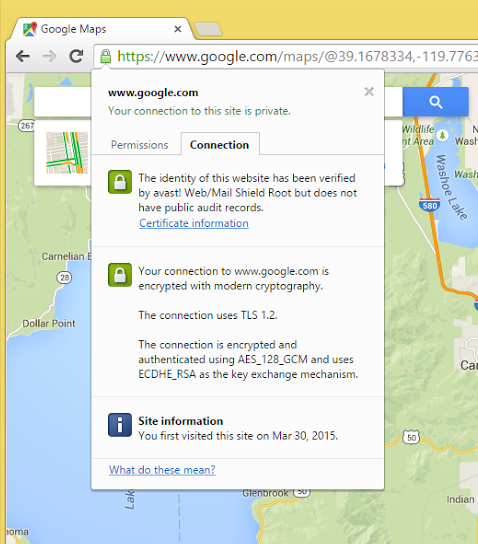
Google Maps showing the Avast! certificate
I case you’re not that familiar with what the connection information is supposed to show you, you can be pretty sure that Google doesn’t have their identity verified by avast!.
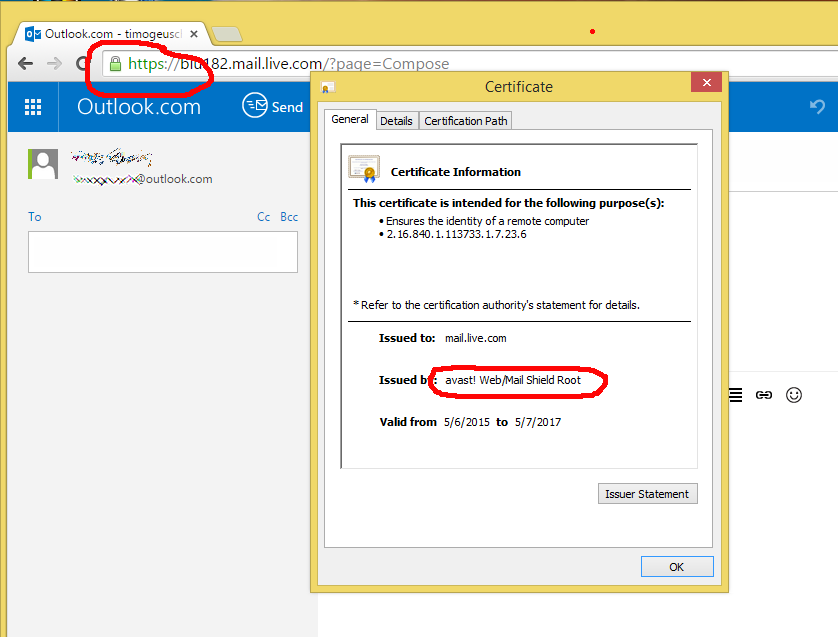
As I was preparing the images for the blog post, I noticed the same behaviour on Outlook.com. Have a look at the “Issued by:” entry for the certificate information and also the encryption information in the URL box:
Now compare the identity information for the “clean” connection with avast! web shield disabled to the information that was showing up in my first example showing Google Maps. This is what a real certificate is supposed to look like:
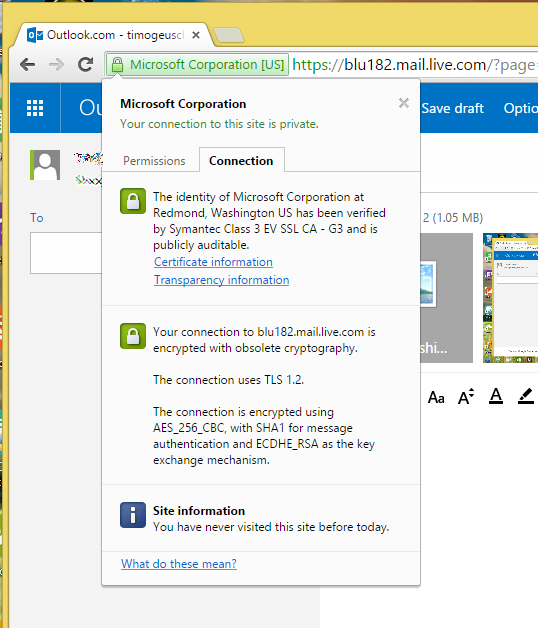
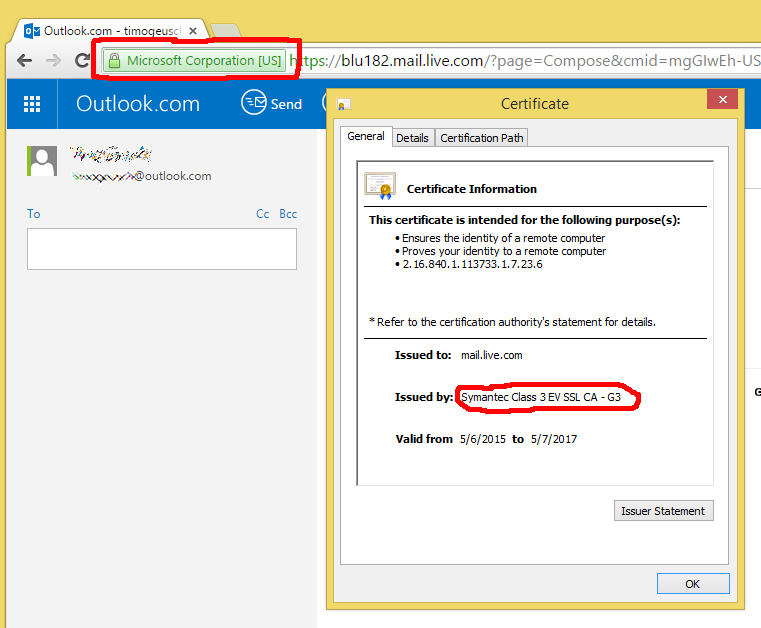
Did you notice the inscription “Microsoft Corporation [US]” next to the padlock symbol that indicates you’re on an encrypted connection? That shows Microsoft is using an EV (Extended Validation) certificate for this particular site. EV certificates are backed by a much more thorough identity verification process, not to mention that they’re considerably more expensive than a normal certificate. EV certificates are intended to give the user additional confirmation that you’re indeed talking to who you think you’re talking to and not Joe’s Phishing & Hijacking service. With avast!’s inserted security certificate, you lose this additional protection. Oh, and for additional comedy value - avast! themselves use an EV certificate on their own website. Which is commendable, only that you don’t necessarily see it if you use the software you downloaded from that website.
Now, is this a big security crisis and we all need to break out our tinfoil hats? I seriously doubt that. In fact, I believe avast! is acting in good faith with their web shield - after all, if you want to protect your users from malware downloaded over an encrypted connection to a dodgy site, the only way to do this in real-time is basically to insert yourself into the connection in the first place.
However, I personally am a bit concerned that Avast! installs a Trusted Root certificate into the Windows certificate store:
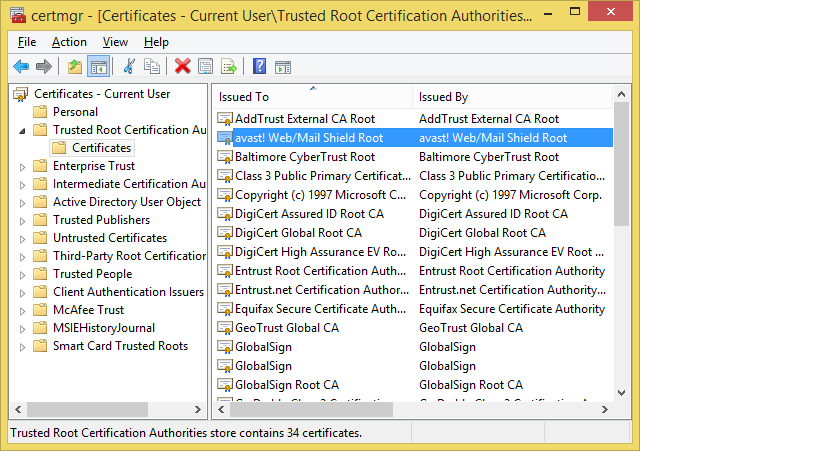
Call it “echos of SuperFish” (see Lenovo’s security advisory here, Google for the tons of spilled electrons on the Internet), but that makes me uncomfortable, especially if the machine you find it on a machine that you use for online banking.
For my part, I’ve turned the web shield https scanning functionality off for now and will probably spend some more time on this sunny afternoon researching alternative virus scanners.
